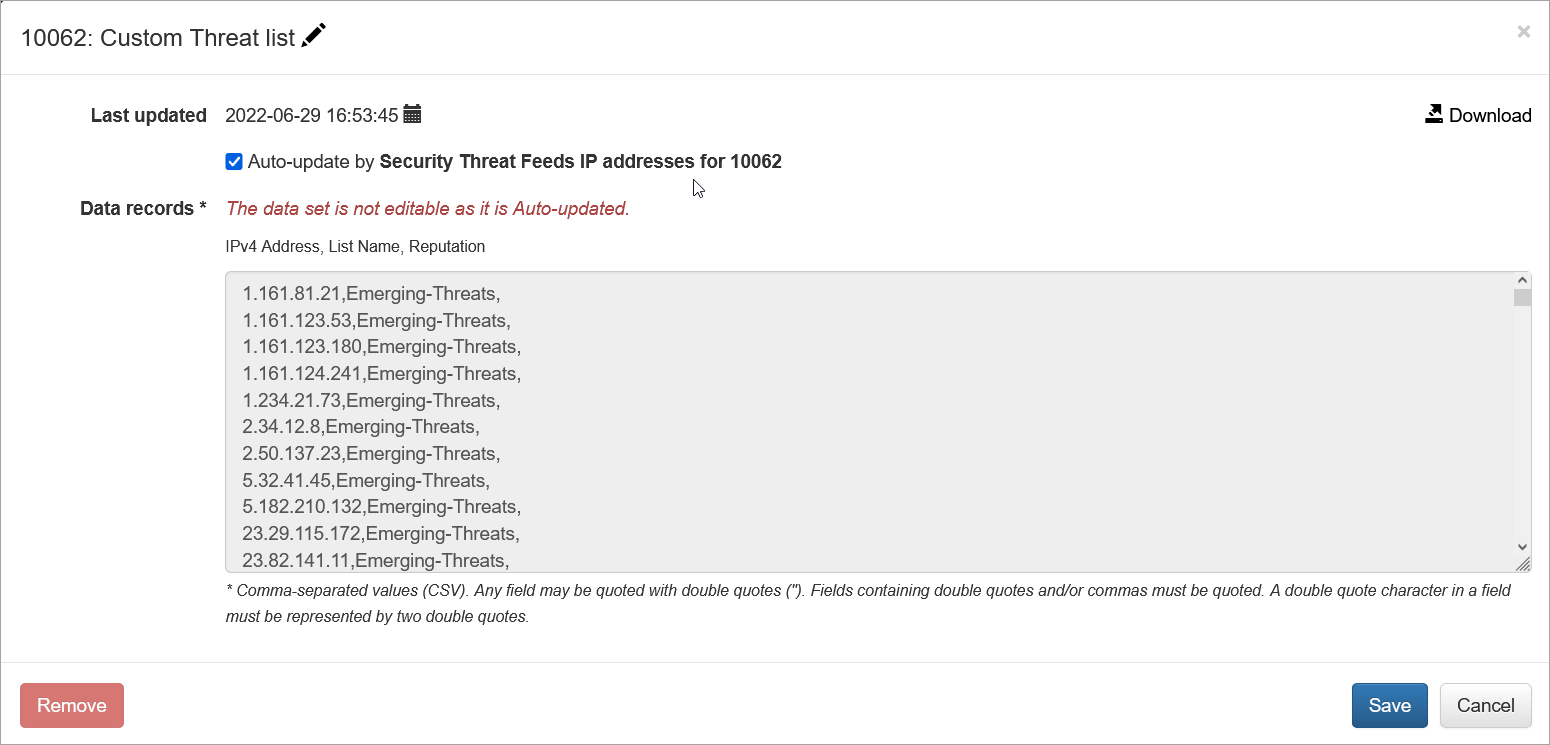
Configuring Custom Threat List
Custom Threat List is a lookup database with the following fields:
- IP address
- List name
- Reputation
Where
- IP address is provided by a threat list vendor or, for lists with malicious domain names (currently supported from AlienVault OTX), determined by NFO using reverse-DNS lookup
- List name is the name of the list specified in configuration
- Reputation is provided by a threat list vendor or, for lists with malicious domain names (currently supported from AlienVault OTX), set by NFO using malicious domain name provided by the list vendor
EDFN Agent Configurations - Settings
Click on Security Threat Feeds IP addresses for 10062.
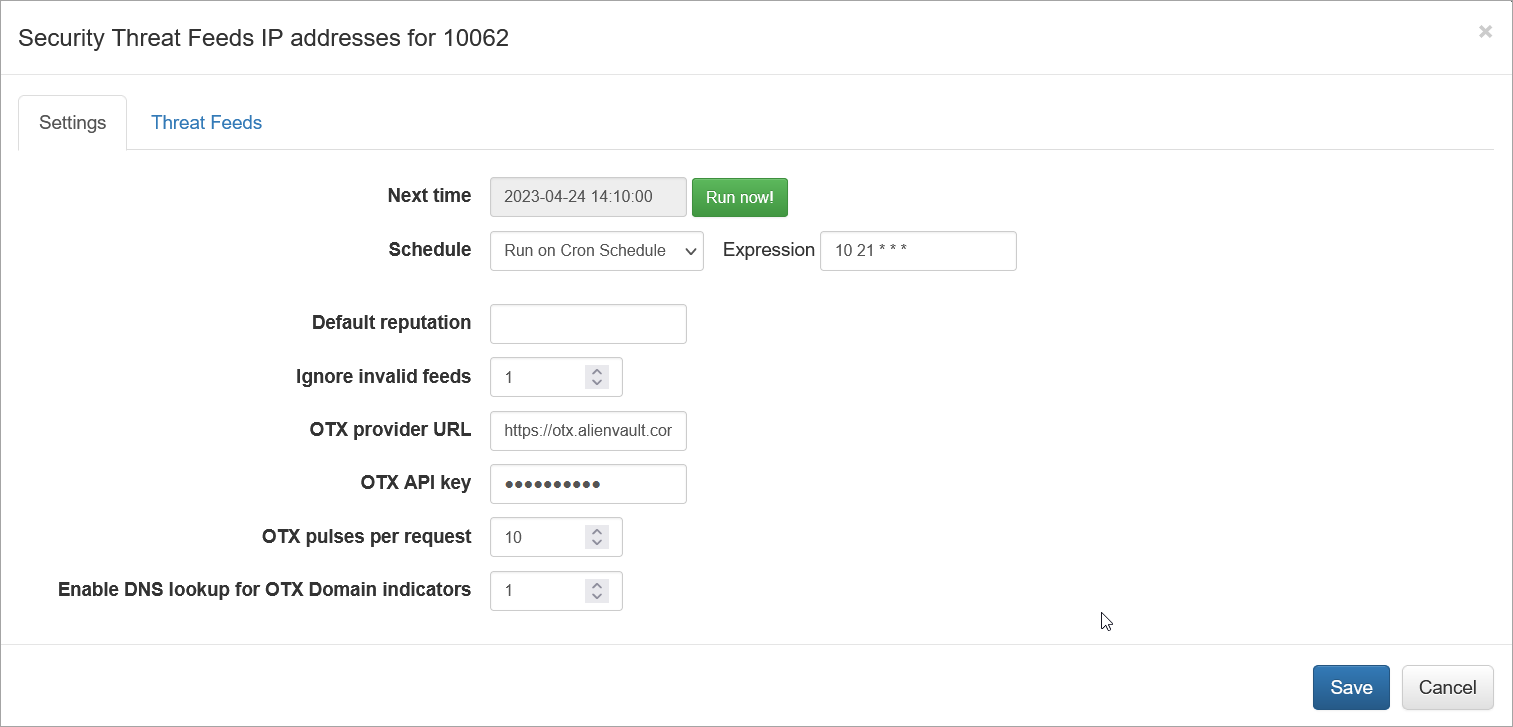
On this screen you can configure the following parameters:
Cron Schedule
All threat lists are updated on cron schedule set here.
Default Reputation
If Reputation is not provided by a threat list vendot, you can set default string here.
The following fields are used for configuration with AlienVault OTX
Ignore Invalid Feeds
If set to 1, AlienVault feeds not containing IP addresses or domain names will be ignored and not imported
OTX Provider URL
AlienVault OTX URL. Default is https://otx.alienvault.com
OTX API key
Your OTX API for OTX Pulses subscription.
All Pulses in your subscription will be imported!
OTX Pulses per Request
Set how manu pulses to import in one iterration. Default is 10.
Enable DNS lookup for OTX Domain indicators
If enabled, NFO will issue reverse DNS lookup to get IP address of malicious domains. Default is 0 (disabled)
EDFN Agent Configurations - Threat Feeds
Select the next tab and configure threat feeds:
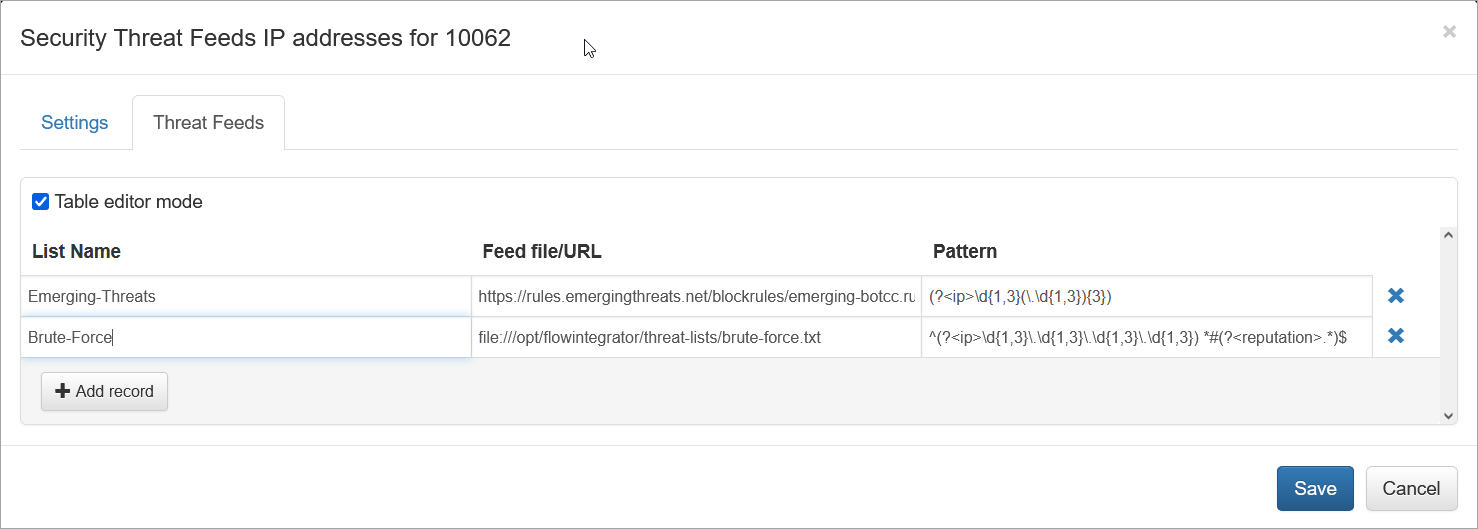
You can add as many feeds as you need by specifying the following:
- List Name
- Feed file/URL
- Pattern
Where
- List name is the name of the list, reported in
threat_list_namefield - Feed file/URL is a pointer to file or URL
- Pattern is a regex expression to extract IP address and Reputation fields from the list
You can use Table editor mode or CSV. Here is an example from above in CSV format:
Emerging-Threats,https://rules.emergingthreats.net/blockrules/emerging-botcc.rules,"(?<ip>\d{1,3}(\.\d{1,3}){3})"
Brute-Force,file:///opt/flowintegrator/threat-lists/brute-force.txt,"^(?<ip>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}) *#(?<reputation>.*)$"
Verifying Configuration
When configuration is completed, save it, then open again and press green Run now button. You should see the list and timestamp updated:

Click on Custom Threat list to view the list. You can also download it from here: