Configure Universal Forwarder Input
Create or modify %SPLUNK_HOME%/etc/system/local/inputs.conf file as follows. In general there are two options, either to listen directly for netflow events on a specific port or optionally to monitor files created by syslog-ng or rsyslog.
Receiving Syslogs Directly from NFO (UDP port 10514)
Add the following lines to inputs.conf file and modify it for your netflow index, if necessary:
[udp://10514]
sourcetype = flowintegrator
index = flowintegrator
Configuring Universal Forwarder with syslog-ng or rsyslog
In this scenario syslog-ng or rsyslog are configured to listen to syslogs sent by NFO on a UDP port 10514. Syslog-ng or rsyslog are usually writing the logs into configurable directories. In this example we assume that those are written to /var/log/netflow.
Add the following lines to inputs.conf file and modify it for your netflow index, if necessary:
[monitor:///var/log/netflow]
sourcetype = flowintegrator
index = flowintegrator
It is very important to set sourcetype=flowintegrator and to point it to the index where V2P Network Visibility for Splunk App and Add-on are expecting it.
Configure Universal Forwarder Output (Target Indexers)
During the installation of the Universal Forwarders a Receiving Indexer can be configured, as it can be seen here:
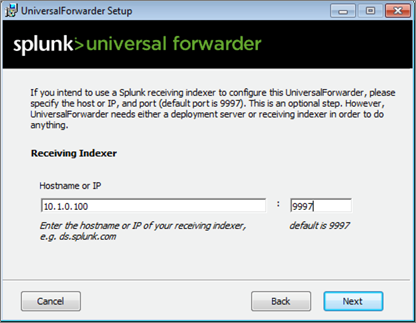
It is an optional step during the installation. If it was not configured or if load balancing is required, additional Receiving Indexers can be added later by adding to the %SPLUNK_HOME%/etc/system/local/outputs.conf file:
[tcpout]
defaultGroup = default-autolb-group
[tcpout:default-autolb-group]
server = 10.1.0.100:9997,10.1.0.101:9997
More info about load balancing: http://docs.splunk.com/Documentation/Splunk/latest/Forwarding/Setuploadbalancingd#How_load_balancing_works