Configuring User Identity Enrichment
Integrating user identity data into flow data enriches the information available for analysis, expediting incident investigations and enhancing overall security measures. By enriching flow data with user identity details, such as username, organizations can swiftly identify suspicious activities, detect unauthorized access, and respond promptly to security incidents. This enrichment enables security teams to gain deeper insights into network behavior and user interactions, ultimately reducing the time required for incident response and bolstering the overall security posture of the network environment.
User identity is provided by EDFN agent User identity monitor and It builds two lookup lists:
- IPv4, idp, username
- IPv6, idp, username
Where
- idp is identity provider that reported IP address and username
- IPv4 is IP address from which the user logged on
- username is the name of the user or account name reported by identity provider
In this release the agent supports the following methods:
- Integration with Active Directory Domain Controller
- Integration with Microsoft Entra ID
- Integration with Okta
- Integration with any identity management system reporting login/logout events via syslog
Configuration Steps
To configure integration with User Identity system, on the left navigation bar select Modules, open Network Conversations Monitor set by clicking on ..., and click on Module configuration 10062: Network Conversations Monitor. Scroll down to EDFN Agent User identity monitor and click on it.
You will be presented with the following configuration screen.
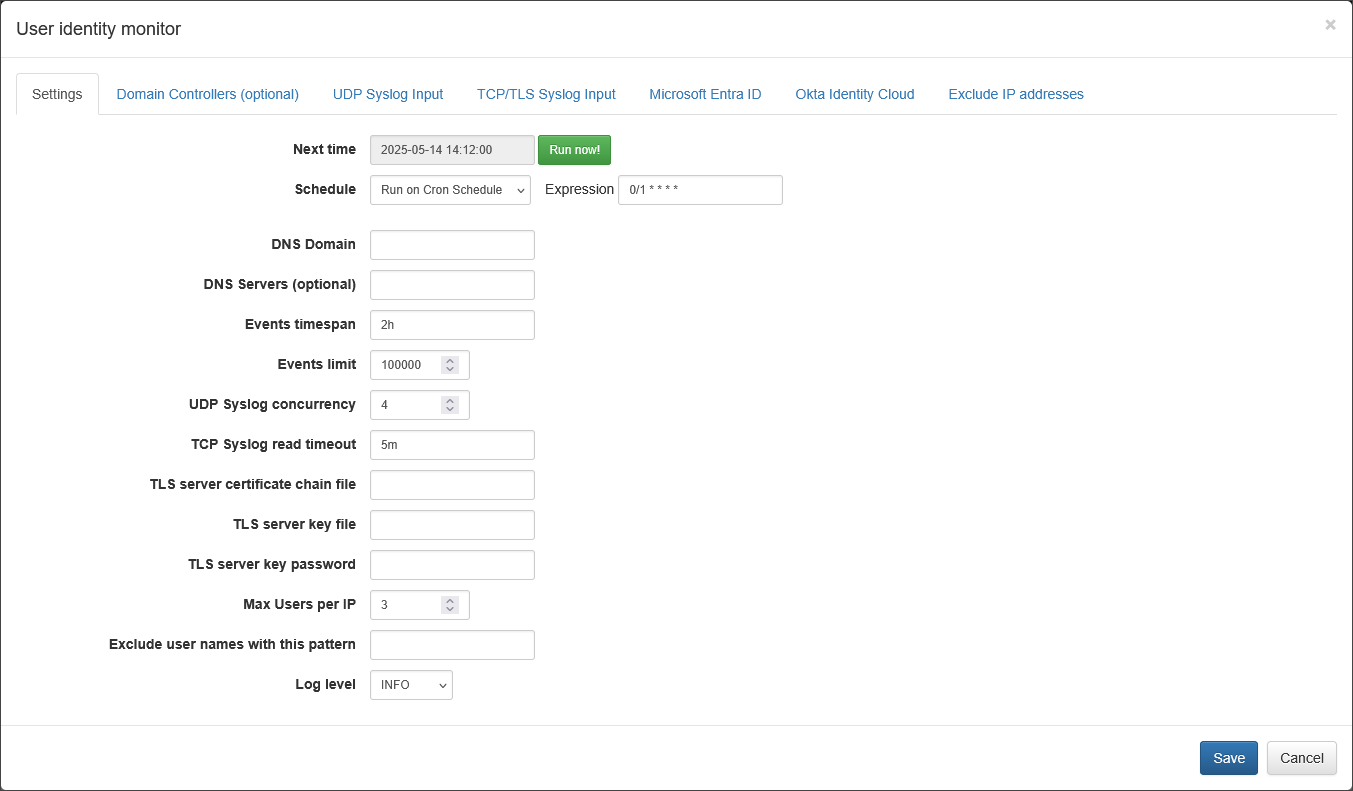
Set common parameters, and select an appropriate tab to configure the intetration with your identity systems.
Select Excluded IP addresses tab to specify IP addresses not to be included in user udentity enrichment, for example your Terminal Server IP address where multiple users are signing from.
Make sure that the user identity fields are included in the Module output.
For details, visit Network Conversations Output configuration