EDFN Administration
The External Data Feeder for NFO (EDFN) is the auxiliary engine that handles communications outside the standard NetFlow/IPFIX protocols. This page covers the administrative management of the EDFN service, including security, connectivity, and service maintenance.
Service Management
EDFN is typically installed alongside NFO. Ensuring the service is running and healthy is the first step in enabling cloud ingestion and data enrichment.
Checking Status
- Linux: Use
systemctl -l status nfi_updd.serviceto verify the service is active. - Windows: Open Services.msc and locate the External Data Feeder for NFO service.
Authentication Configuration
Default instalation directories are:
$NFO_HOME - /opt/flowintegrator
$EDFN_HOME - /opt/nfi-updater
Self-signed certificate is already installed in $EDFN_HOME/conf/.updater_keystore, the keystore password is password and private key password is the same.
To change the default password, see Changing the Keystore Password section below.
External Data Feeder for NFO is authenticated to NetFlow Optimizer as the user updater using X509 certificate. This user only has access to data sets maintenance. This X509 certificate is generated during the first NFO installation or upgrade to release 2.10.
If you need to change it, follow the instructions below.
X509 Authentication
Procedure
Create a Certificate Signing Request (CSR) with keytool and generate a Signed Certificate for the CSR:
- Delete previous certificate:
$EDFN_HOME/java/jre/bin/keytool -delete -alias updater -storepass password ‑keystore
$EDFN_HOME/conf/.updater_keystore
$NFO_HOME/java/jre/bin/keytool -delete -alias updater -storepass password
$NFO_HOME/tomcat/conf/.truststore - Generate the key pair:
$EDFN_HOME/java/jre/bin/keytool keytool -genkey -alias updater -dname "CN=updater, OU=, O=, L=, ST=, C=" -validity 365 -keyalg RSA -keysize 1024 ‑storepass password -keypass password -keystore
$EDFN_HOME/conf/.updater_keystore - Generate the Certificate Signing Request:
$EDFN_HOME/java/jre/bin/keytool -certreq -alias updater -keyalg rsa -storepass password -keystore
$EDFN_HOME/conf/.updater_keystore -file updater.csr - Generate a signed certificate for the associated Certificate Signing Request.
- Import the CA certificate into the NetFlow Optimizer keystore:
$NFO_HOME/java/jre/bin/keytool -import -alias root -file CA.crt -keystore ‑storepass password
$NFO_HOME/tomcat/conf/.truststore - Import the signed certificate for the associated updater alias in the keystore:
$NFO_HOME/java/jre/bin/keytool -import -alias updater -file updater.crt ‑keystore -storepass password
$NFO_HOME/tomcat/conf/.truststore
Self-Signed certificate can be exported instead of steps 3-5:
$EDFN_HOME/java/jre/bin/keytool -export -alias updater -storepass password ‑keystore
$EDFN_HOME/conf/.updater_keystore -file updater.crt
Notes:
- Certificate CN field value must be updater.
- If keystore type, keystore password, key password or key algorithm were changed, these changes have to be added to the
$EDFN_HOME/conf/updater.propertiesfile:
keystoreFile = ../conf/.updater_keystore
keystoreType = jks
keystorePass = password
keyPass = password
keyAlgorithm = SunX509
Import the Certificate into External Data Feeder for NFO truststore
NFO and External Data Feeder for NFO use secure connection (https) for communication. Tomcat certificate and root chain are imported automatically into $EDFN_HOME/conf/.updater_truststore during first connection. If tomcat certificate is changed, it should be reimported into .updater_truststore file manually or .updater_truststore can be removed (it will be recreated after External Data Feeder for NFO service restart).
Procedure
To reimport the certificate perform the following:
- Enter the following commands to delete previous certificate(s):
- Get list of current trusted certificates:
$EDFN_HOME/java/jre/bin/keytool -list -keystore $EDFN_HOME/conf/.updater_truststore- Delete all certificates from the previous step:
$EDFN_HOME/java/jre/bin/keytool –delete –alias <crtAlias> -keystore $EDFN_HOME/conf/.updater_truststore - Enter the following command to import the chain certificate into the External Data Feeder for NFO truststore:
# $EDFN_HOME/java/jre/bin/keytool -import -alias root -keystore $EDFN_HOME/conf/.updater_truststore -trustcacerts -file rootCA.crt - Enter the following command to import tomcat certificate into the External Data Feeder for NFO truststore:
# $EDFN_HOME/java/jre/bin/keytool -import -alias tomcat -keystore $EDFN_HOME/conf/.updater_truststore -file srv.crt - After these actions External Data Feeder for NFO service should be restarted.
Changing the Keystore Password
This section outlines the procedure for updating the keystore passwords used by the External Data Feeder for NFO (EDFN).
Prerequisites
- Administrative access to the server where EDFN is installed.
- Knowledge of the current keystore passwords. Default passwords are
password.
- Backup: Before making any changes, it is highly recommended to create a backup of both the
.updater_keystore,.updater_truststore,.cacerts, andupdater.propertiesfiles in/opt/nfi-updater/confdirectory. - Upgrades: When performing an NFO/EDFN upgrade, the
updater.propertiesfiles may be overwritten. You will need to re-apply these password changes and other custom configurations after the upgrade is complete. - Consistency: Ensure that the new passwords in the
updater.propertiesfile exactly match the passwords you set usingkeytool.
Instructions
-
Navigate to the EDFN configuration directory:
cd /opt/nfi-updater/conf/ -
To change the password for the
.updater_keystore, use thekeytoolcommand. You will be prompted to enter the current password and then the new password./opt/flowintegrator/java/jre/bin/keytool -storepasswd -keystore .updater_keystore -
Similarly, change the password for the
.updater_truststoreusingkeytool. You will be prompted for the current and new passwords.keytool -storepasswd -keystore .updater_truststore -
Finally, if you have
.cacertsfile, change the password for the.cacertsusingkeytool. You will be prompted for the current and new passwords.keytool -storepasswd -keystore .cacerts -
Update the
updater.propertiesfile to reflect the new passwords. Open the file for editing:vi updater.properties -
Change
updater.propertiesparameters keystorePass, keyPass, truststorePass, and cacertsPass to your new password. -
Save the
updater.propertiesfile and exit the editor. -
Restart the EDFN service for the changes to take effect.
- On Linux, use the appropriate command for your system (e.g.,
systemctl restart nfi_updd.service). - On Windows, restart the
NFOUSvcservice.
- On Linux, use the appropriate command for your system (e.g.,
What to do next
If certificate is imported automatically (.updater_trustore created automatically), certificate can be verified using following command:
$NFO_HOME/java/jre/bin/keytool -list -v -keystore $EDFN_HOME/conf/.updater_truststore
You can change .updater_truststore type, password and path configuration in the $EDFN_HOME/conf/updater.properties file.
Proxy Server Configuration
If your NFO appliance is in a restricted network zone (common in enterprise environments), EDFN must be configured to use a proxy to download Threat Intel updates or reach Cloud APIs (AWS/Azure).
Procedure
- On the left navigation bar select
External Data Feederand clickProxy settings.
- Specify your Proxy Server parameters.
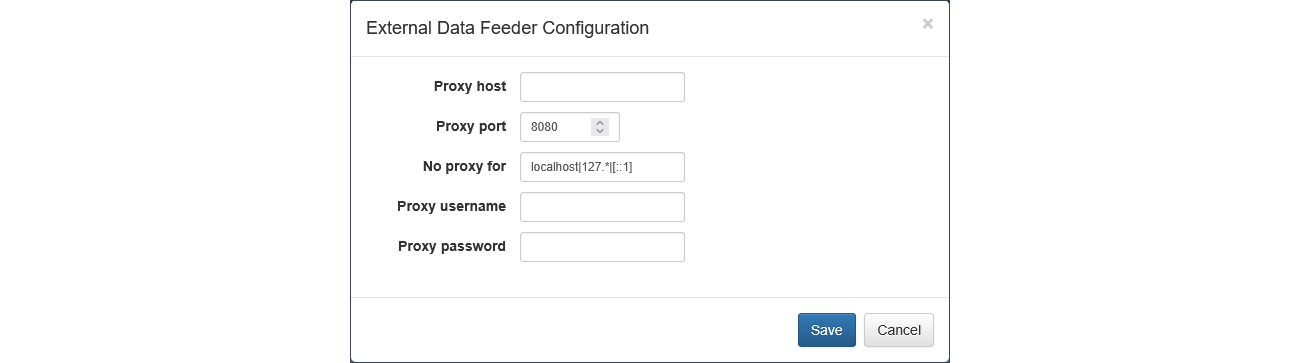
- Press Save button to save your settings
Importing HTTPS Certificates
When your external data sources or targets require secure HTTPS/TLS communication, you may need to import their corresponding certificates into NetFlow Optimizer's trust store. This procedure ensures NFO can establish secure and trusted connections.
NetFlow Optimizer strictly accepts TLS certificates where the subjectAlternativeName (SAN) field contains a DNS name or an IP Address value that correctly matches the data source hostname or IP address.
When you generate certificate using openssl, make sure you specify the following parameter:
-addext "subjectAltName=DNS:example.com,IP:10.0.0.1"
Procedure
Follow these steps to import HTTPS certificates:
-
Obtain the Certificate Chain: You can download the certificate chain from your data source using a web browser or the openssl command-line tool:
openssl s_client -connect <ip-or-fqdn>:443
If using openssl, save the entire certificate chain (concatenate all sections from -----BEGIN CERTIFICATE----- to -----END CERTIFICATE----- for each certificate in the chain) to a single .pem or .crt file.
- Access Certificate Management in NFO:
Navigate to the External Data Feeder on the left bar.
Click "Manage HTTPS/SSL certificates" and upload an actual certificate (root CA or a full chain).
- Upload and Import the Certificate:
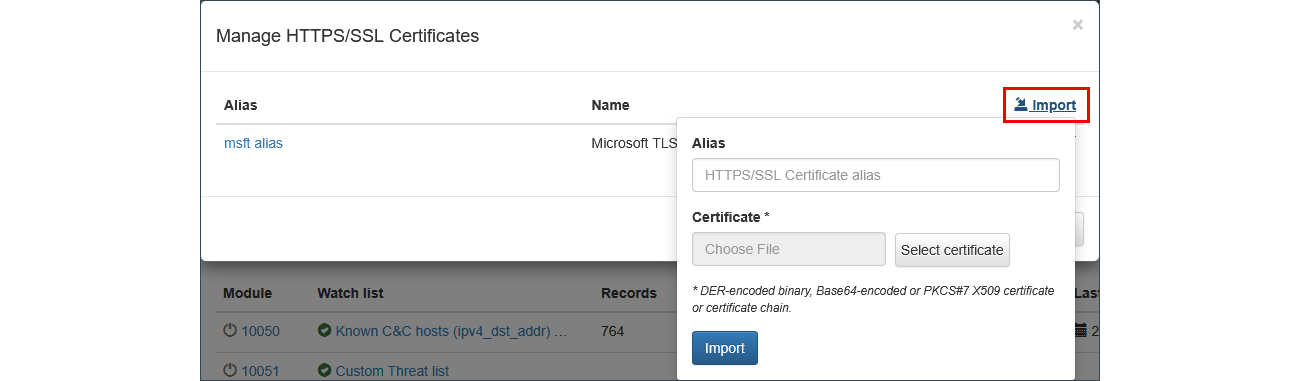
- Press Save button to to apply the new certificate configuration.
Copying Configuration
This section is relevant in scenarios where EDFN is installed on a different machine from NFO. It describes how to copy EDFN configuration from machine A to B. We assume that EDFN is already installed and configured on machine A. EDFN stores all configuration in the installation directory and in the NFO data base, so it can be simply copied from machine A to B.
Procedure
Use the following steps to do this on Linux:
On machine A:
- Stop EDFN service
- Linux:
systemctl -l stop nfi_updd.service. - Windows: Open Services.msc and locate the External Data Feeder for NFO service and stop it.
- Linux:
- Create copy of installation:
tar -czf NFO-updater_copy.tar.gz /opt/nfi-updater - Start EDFN service
- Copy
NFO-updater_copy.tar.gzto B.
On machine B:
- Install same version of EDFN as on A. Don’t configure EDFN.
- Stop EDFN service
- Remove all EDFN files:
rm -rf /opt/nfi-updater - Extract copy of EDFN:
tar -xzf nfo-updater_copy.tar.gz -C / - If EDFN on B should use different client certificate or tomcat has different certificate, reconfigure
.updater_keystoreor.updater_truststorerespectively. - Set uri property in the
/opt/nfi-updater/conf/updater.propertiesfile. - Start EDFN service
- Check that EDFN has been started (see Status -> History panel in the GUI, logs should contain line like INFO[updater] Updater<updaterUID> (x.x.x.x.x) connected).
Where to find Data Configuration?
Looking for how to configure specific data sources? Please refer to the following sections:
- To configure AWS, Azure, GCP, or Oracle flow Logs, see Data Ingestion > Cloud Flow Logs.
- To configure Threat Intel, GeoIP, or vCenter, see Data Enrichment.