NetFlow and SNMP Analytics for Splunk
Introduction
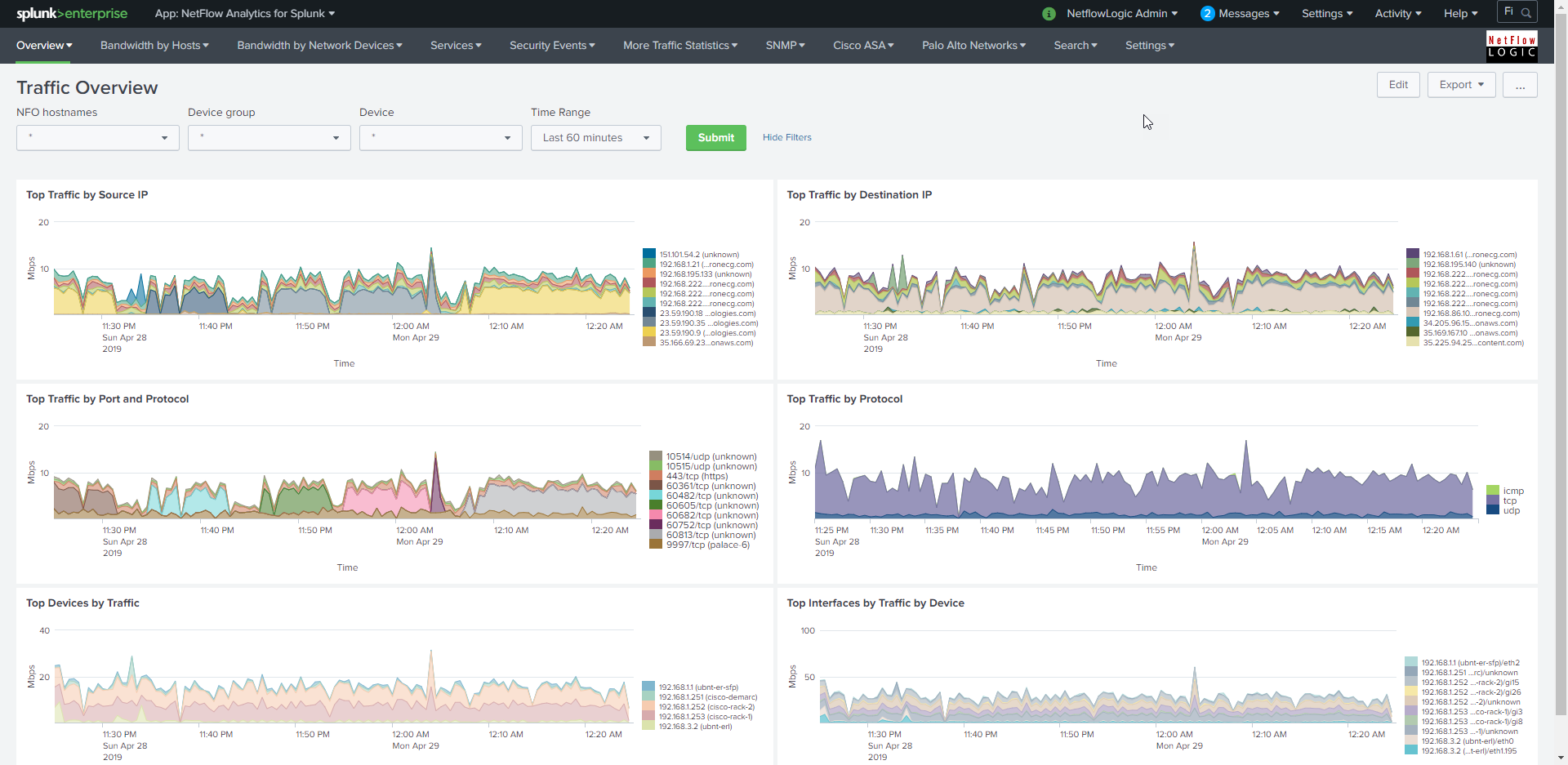
NetFlow Analytics for Splunk App is designed to deliver next generation, real-time, network resource management power to network and security analysts. NetFlow Optimizer™ (“NFO”) is a middleware that processes massive amount of flows (NetFlow, sFlow, IPFIX, etc. on premises, as well as VPC Flow logs in the Cloud) to stream summarized and meaningful CIM (“Common Information Model”) compliant syslog (or JSON) events into Splunk Enterprise or Splunk Cloud, and, optionally, all original flow records to inexpensive syslog storage, such as your rsyslog, syslog-NG, Elastic, or Hadoop cluster. The events are available for alerting and correlation with other machine data. NetFlow Analytics for Splunk App (“App”) provides visualization and reporting capabilities. The operators benefit from detailed visibility to their entire network and being able to address many IT use cases including bandwidth monitoring, capacity planning, congestion troubleshooting, and cyber security using threat intelligence lists.
The App includes Cisco ASA, Palo Alto Network, and VMware NSX firewall flow data dashboards which present bandwidth usage, users, applications, and violators etc., enabling the continual reinforcement of firewall policies.
The App also includes a number of dashboards for monitoring and security of your mission-critical applications across all regions and accounts on cloud platforms like Microsoft Azure, AWS, Google Cloud Platform, as well as hybrid cloud infrastructures.
As NFO supports SNMP polling and traps, the App contains dashboards and alerts to view your hardware infrastructure and be notifies of failures and events needed IT operations attention.
This guide is intended for network and security analysts who use the App to monitor and investigate problems. For additional NFO information please visit www.netflowlogic.com.